IaC-Based Automated Deployment of DBSAFER Stack
Learn how to instantly deploy a secure DBSAFER environment on AWS with just a single click, without engineer visits or complex configurations.
[AWS] Deploy Security Solutions with a Single Click: No Engineer Visits Required
Introduction
Did you assume that implementing high-level security solutions in financial, public, or enterprise environments necessitates long lead times and complex procedures?
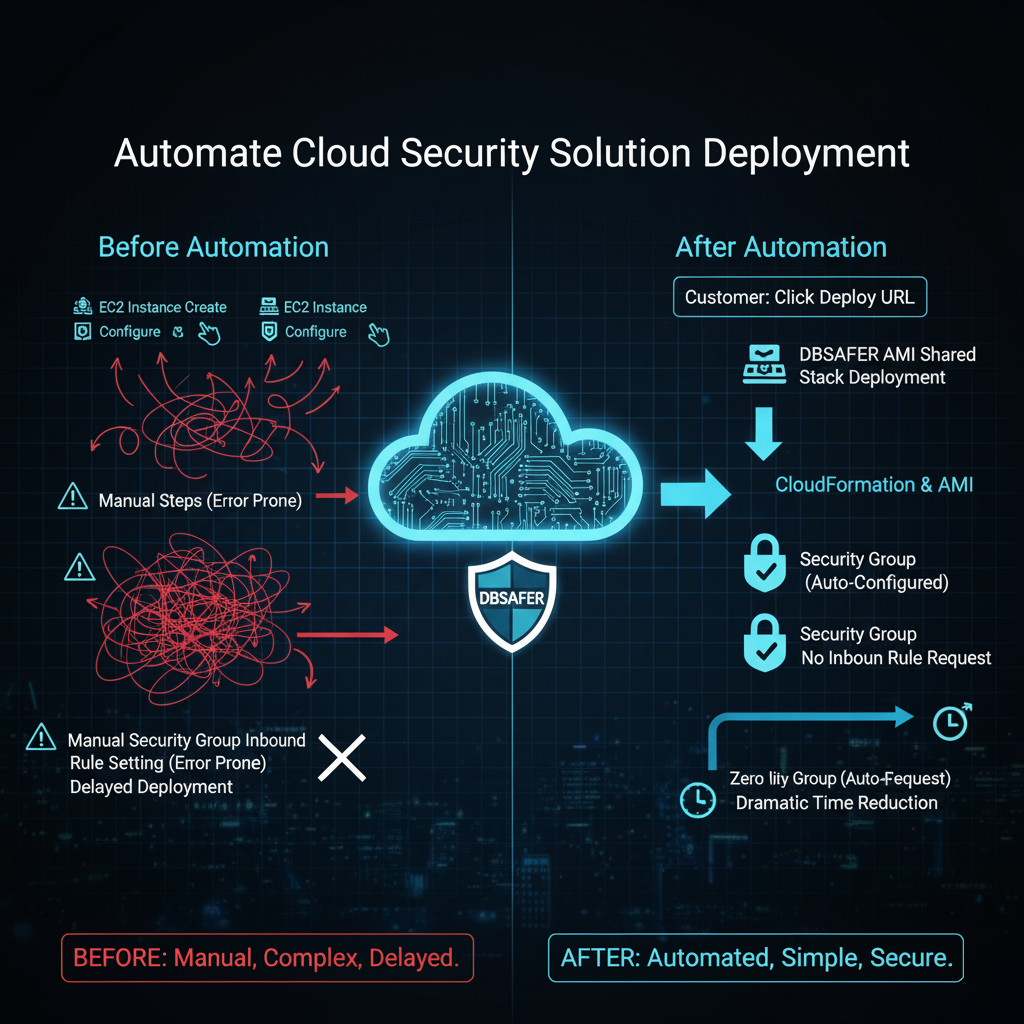
Subscribing to security solutions in a cloud environment should be more than just changing the installation method; it must be a process that innovates Customer Experience and operational efficiency. We are introducing an automated deployment process that radically improves burdensome installation procedures, allowing customers to adopt DBSAFER safely and quickly without needing face-to-face engineer support.
Background
The difficulties customers faced when adopting security solutions in the past were clear:
- Security Risks: Since engineers needed access to customer servers for installation, there was the burden of sharing sensitive access credentials (such as PEM keys) with external parties.
- Communication Fatigue: Installations often halted until firewall (Security Group) ports were opened, or rework was required due to incorrect port configurations.
- Long Wait Times: Manual procedures, ranging from EC2 creation to package installation, often led to unstable initial environments and schedule delays.
To resolve these inconveniences, PNPSECURE introduced a new deployment method utilizing AWS-native tools: AMI (Amazon Machine Image) and CloudFormation.
Implementation: Automation Structure Using AMI & CloudFormation
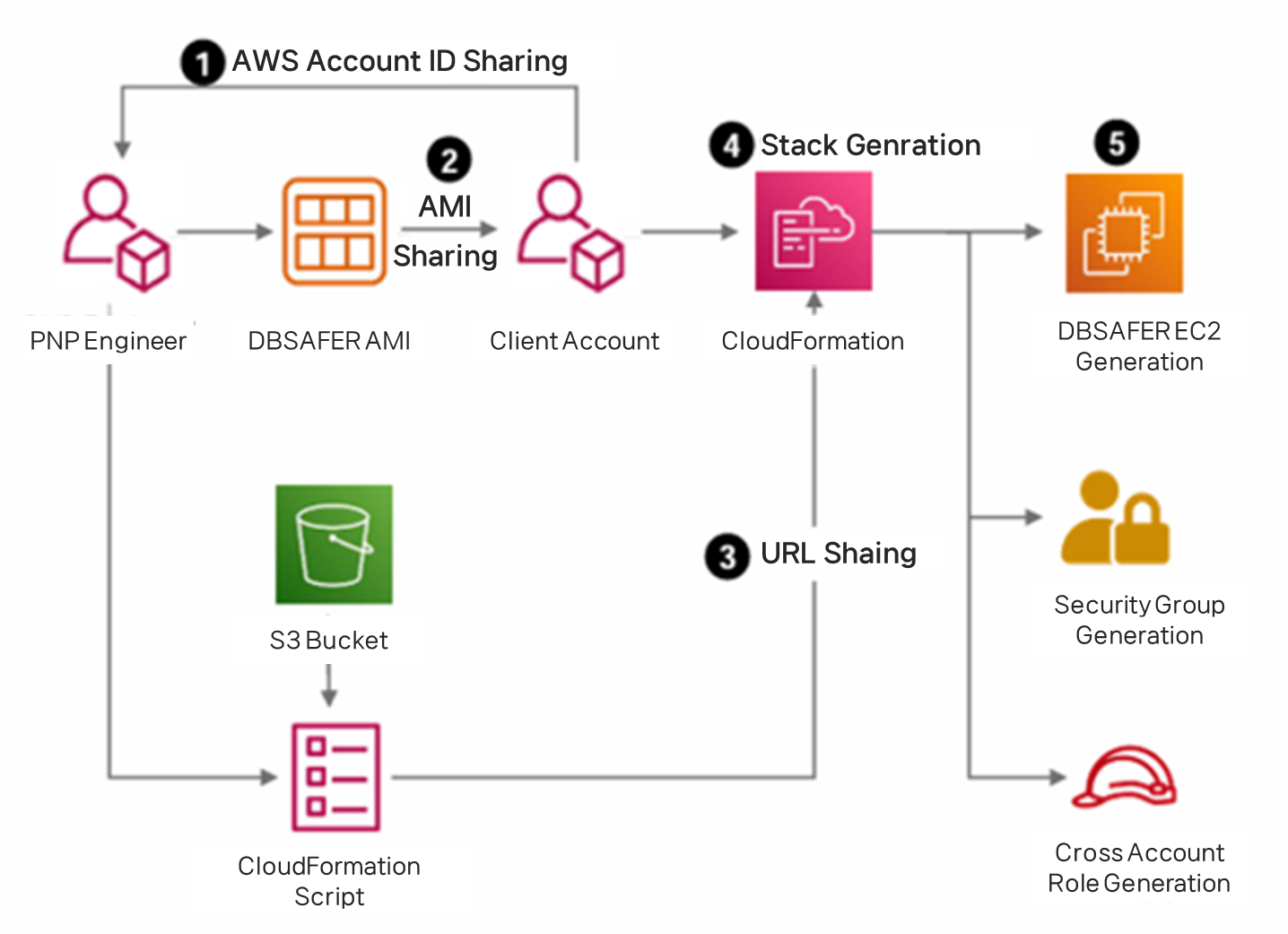
Sharing Standardized Images (AMI)
Upon a subscription request, PNPSECURE grants DBSAFER AMI usage permissions solely to the customer's AWS Account ID. Customers do not need to download or verify separate installation files; they can immediately use a pre-configured and verified Standardized Image
CloudFormation Stack Deployment
The engineer provides a CloudFormation URL containing the deployment code to the customer. The customer simply accesses this URL and selects just three items:
- Select VPC and Subnet for installation
- Specify EC2 Instance Type
- Set Basic Security Group
With just a few clicks, the entire security infrastructure, including EC2 instances, IAM Roles, and network settings, is automatically generated.
Deployment Results
When CloudFormation is executed, the following tasks are completed automatically:
- Creation of EC2 instances
- Auto-configuration of Security Groups, IAM Roles, and Network settings
- Automated Security Group Settings: Inbound rules required for DBSAFER operations are automatically applied, eliminating the need for administrators to request port openings separately.
This significantly reduces installation delays and errors, providing a much smoother deployment experience.
Expansion and Demonstration
We have secured technical scalability beyond simple deployment.
- Expanded to a Silo-based SaaS model utilizing AWS SaaSBoost.
- Optimized through collaboration with AWS developers.
- Verified technical maturity through demonstrations at the DBSAFER AWS Summit and registration in the Private Market.
Benefits
Zero External Access
The biggest change is that "external engineer access" is no longer necessary. Customers can achieve the same results as an expert installation by simply providing an Account ID and clicking a URL, without handing over infrastructure access rights. This makes compliance with internal security regulations much easier.
Zero Human Error
We fundamentally block "misconfigurations," a primary cause of cloud security incidents. Security Group inbound rules essential for DBSAFER operation are set automatically upon deployment. Administrators no longer need to worry about service outages or security holes caused by missing or incorrectly opened ports.
Zero Wait Time
Immediate adoption is possible at the customer's desired time without coordinating engineer schedules. In fact, while DBSAFER deployment cases increased by about 50 (120 → 170 cases) in 2024 compared to the previous year using this method, we were able to provide stable support without delays. This signifies that customers have secured the flexibility to immediately scale out in line with their business expansion.
Conclusion
IaC-based automated deployment is not just a technical improvement. It is an evolution of the service model that provides practical convenience—reducing installation effort to zero—and guarantees operational stability from the initial setup stage.
Now, PNPSECURE's engineers are moving away from repetitive installation tasks to focus on higher-value technical support, such as operational optimization and security consulting for our customers.
