FaceLocker: Vision AI-Powered Authentication Security
FaceLocker provides facial recognition-based passwordless login and screen protection, enhancing security and business continuity in enterprise Zero Trust 2.0 environments.

Table of Contents
- Introduction: Information Security Threats and Role of Vision AI
- Key Terms in Vision AI and Authentication
- Introducing FaceLocker
- Core Values
- Key Features
- FaceLocker Technical Architecture
- Tech Stack
- Client Architecture
- Server Components
- Detailed Features of FaceLocker
- Windows Login
- Anomaly Detection and Control
- Watermark Implementation
- Other Key Features
- Zero Trust Security Model and FaceLocker
- Specifications, Performance, and Scalability
- Specs
- Performance and Scalability
- Compliance and Regulatory Overview
- Recommendations
1. Introduction: Information Security Threats and Role of Vision AI
As digitalization progresses, data leakage incidents continue to increase.
According to the 2024 Verizon Data Breach Report, a total of 30,458 security incidents were investigated, with 10,626 cases involving data breaches and 2,961 caused by social engineering attacks.
Within South Korea, information and technology leakage incidents are rising across public, private, and financial sectors. Password-based authentication vulnerabilities, insider/external filming, and remote work screen-sharing risks highlight the need for advanced protection using biometric and Vision AI technologies.
The '3M Visual Hacking Experiment' showed that 23% of total information and 53% of sensitive data could be captured from screens.
Vision AI can detect and block unauthorized data capture in real-time, providing proactive protection against visual hacking.
Vision AI enables computers to analyze and understand images and videos, extracting meaningful information similar to human visual recognition.
It can monitor user activity through webcams and sensors, verifying identity and blocking unauthorized recording or access.
2. Key Terms in Vision AI and Authentication
Vision AI (Vision Artificial Intelligence)
- Analyzes images/videos to extract meaningful information
- Detects faces, eyes, and motion patterns similar to human vision
- Used for identity verification and detecting unauthorized access/recording
Face Recognition Authentication
- Identifies individuals using facial features
- Core component of passwordless authentication
- Compliant with KISA K-NBTC standards, includes anti-spoofing technology
Continuous Authentication
- Monitors user state continuously after login
- Implements real-time policies: screen lock, watermarking, logging
- Key method in Zero Trust 2.0 "Implicit Continuous Authentication (ICA)"
Anti-Spoofing
- Detects and blocks attempts using photos, videos, or masks
- Uses RGB/IR depth analysis, eye blink, and face movement detection
PassKey Authentication
- FIDO standard-based authentication
- Biometric data not stored on server, secure against breaches
Visual Hacking
- Capturing sensitive information via screen observation or recording
- Studies: 88% success rate in experiments; 53% of sensitive data visible
3. Introducing FaceLocker
FaceLocker is a Vision AI-based facial authentication and real-time anomaly detection platform.
It provides Windows login replacement (passwordless), ICA, screen exposure prevention, watermarking, PassKey alternative authentication, fulfilling Zero Trust 2.0 requirements.
Core Values
- Passwordless + ICA: Seamless user experience with continuous monitoring
- Unauthorized Detection & Screen Protection: Policies applied automatically when an unauthorized person or recording is detected
- Enterprise Integration: AD/HR DB/SSO integration, VDI compatibility, centralized policy & log management
- Compliance & Certification: KISA K-NBTC facial recognition, Zero Trust 2.0, financial biometric guidance
Key Features
- Biometric face authentication (Passwordless + ICA)
- Screen exposure prevention against unauthorized personnel
- Anti-Spoofing (photo/video detection)
- Windows login replacement
- Enterprise account integration
- Compliance support
- Low system resource usage
- Supports multiple camera types
4. FaceLocker Technical Architecture
Tech Stack
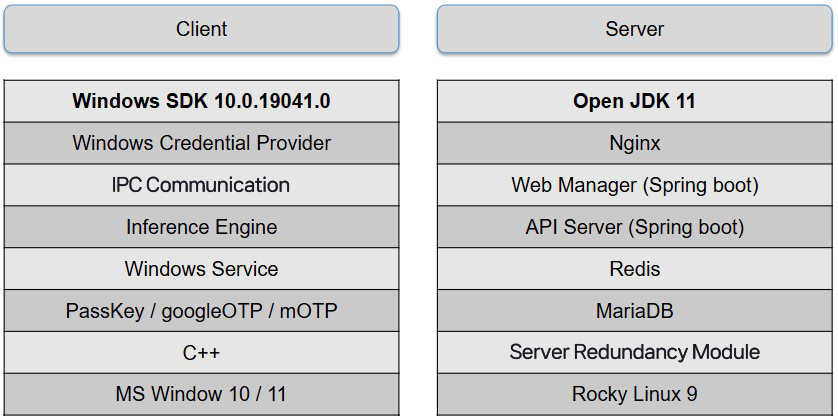
Client Architecture
- Windows Credential Provider (CP): Performs primary authentication, sends inference results to WinLogon
- Windows Service (Agent Core): Background policy enforcement
- Inference Engine (Vision AI): Real-time face authentication, liveness, anomaly detection
- IPC Layer: Asynchronous event communication between CP ↔ Service ↔ Inference
- Alternative Authentication Module: Supports PassKey/Google OTP/mOTP
Server Components
- Nginx: TLS termination, load balancing
- Web Manager (Spring Boot): Policy, user, device, license management
- API Server: Agent communication, authentication events, policy distribution
- Redis: Session & policy cache, temporary job queue
- MariaDB: User, policy, log storage
- Server Redundancy: HA setup for uninterrupted operation
5. Detailed Features of FaceLocker
Windows Login

- Passwordless login via face, AD integration, PassKey support
- Continuous authentication for remote and external environments
Anomaly Detection and Control
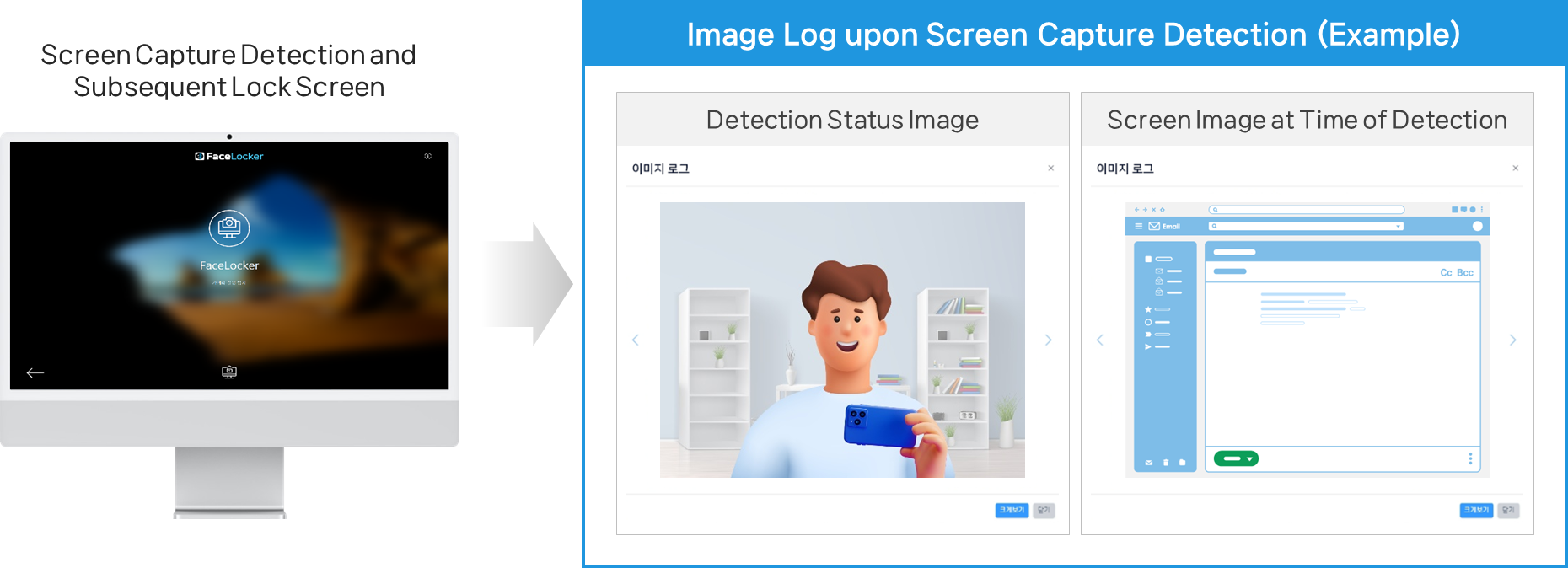
- Detection categories: screen recording, unauthorized presence, idle, webcam obstruction, additional monitors/webcams
- Policy response: screen lock, login screen switch, watermark display
- Audit tracking: user images, screen capture logs
- Multi-display control: prevents output on non-primary monitors
Watermark Implementation
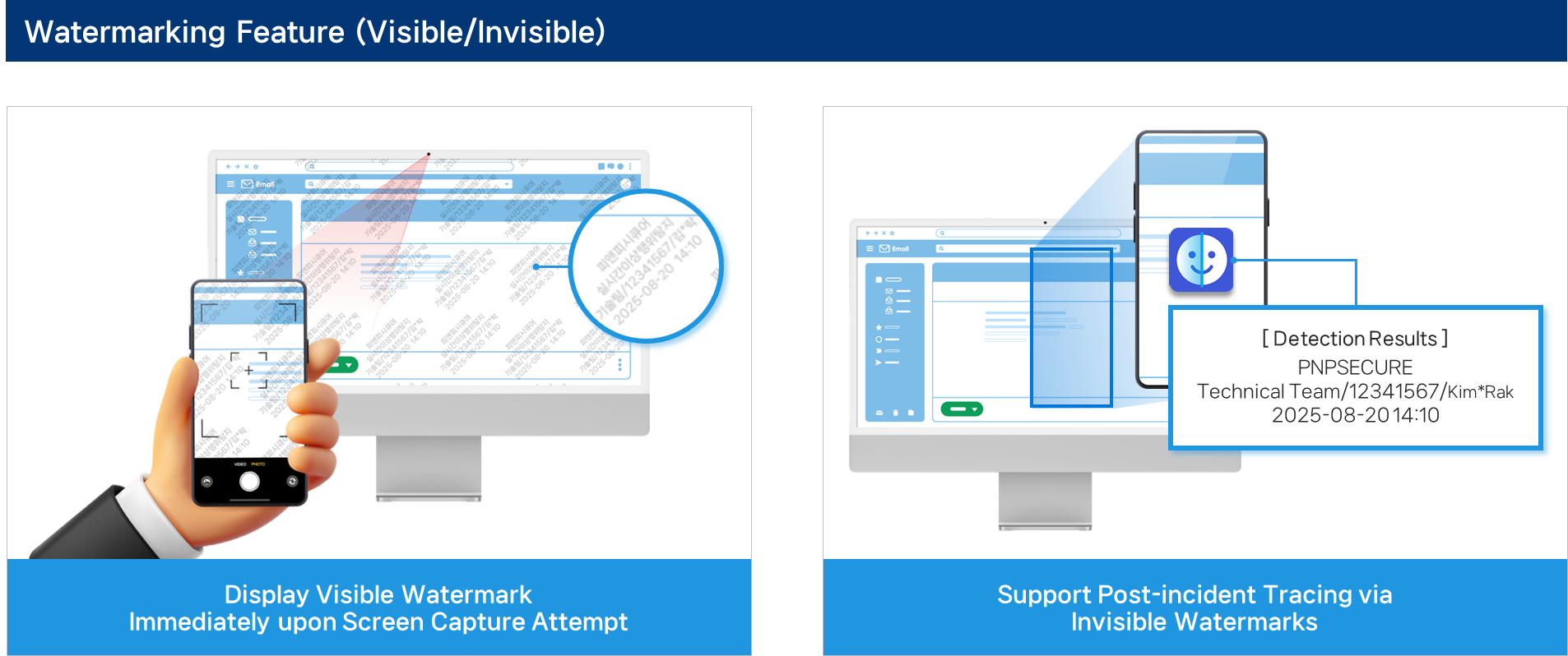
- Visible watermark: displays user info for deterrence and traceability
- Invisible watermark: hidden but tracks leaked images
- Policy/operation: configurable per user/department, can combine with anomaly scenarios
Other Key Features
- Alternative authentication (PassKey/OTP/Email)
- VDI compatibility (VMWare, Citrix, etc.)
- Centralized management & audit
- Offline login (policy-based)
6. Zero Trust Security Model and FaceLocker
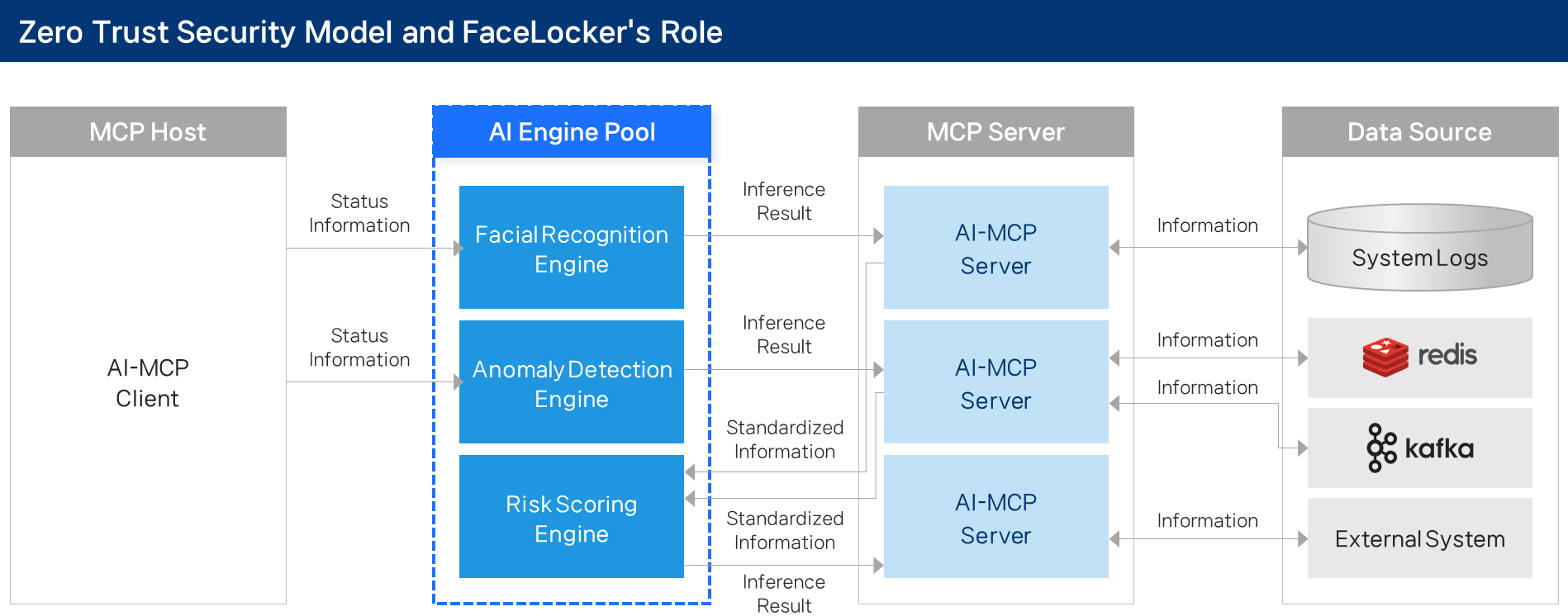
- Requires real-time evaluation of user/device state
- AI-MCP server-client ensemble for risk scoring, continuous authentication
- FaceLocker logs/events serve as trust signals
- Future development: risk scoring engine integration
Zero Trust KPI Examples
- Session security: auto-lock events, multi-person/recording detection events
- Account protection: password login ratio, PassKey+face login ratio
- Organizational control: logged policy violations, top anomaly events
7. Specifications, Performance, and Scalability
Specs
Client Minimum Requirements
- OS: Windows 10 1903+ / 11
- CPU: Intel i5 11th Gen+
- RAM: 8GB+
- Graphics: Intel Iris Xe
- Webcam: HD, UVC 1.0+
- MacOS 11+ (planned 2025.4Q)
Recommended Server Requirements
- OS: RHEL 9.X+
- CPU: Intel Xeon 2.1GHz 12Core+
- RAM: 32GB+
- HDD: 4TB+ (RAID recommended)
- NIC: 1Gbps 2Port+
Performance & Scalability
- Avg. memory usage <500MB, detection <0.5s, CPU <10%
- Windows/MacOS support
- Local/VDI/RDP environment
- Deployable on-premises or cloud with HA
8. Compliance and Regulatory Overview
- Industrial Technology Protection Act: up to 6.5B KRW fine for overseas leakage
- Unfair Competition Prevention Act: up to 1.5B KRW fine, max 15 years imprisonment for trade secret leaks
- Financial Security Institute: Biometric authentication guidance, internal control enforcement
9. Recommendations
FaceLocker delivers face authentication, anomaly detection, and screen recording prevention using Vision AI.
Integrates with existing enterprise authentication and PassKey for unified login.
Enhances security for remote and smart office environments and can serve as a next-gen security gateway.
For detailed features and policy options, refer to documentation or contact sales@pnpsecure.com
