Hybrid Environment Infrastructure Security Approach
Explore a proven DBSAFER architecture for unified access control in hybrid environments, ensuring security, efficiency, and compliance across cloud and on-premise resources.

Digital transformation is breaking down the boundaries of enterprise infrastructure. Hybrid environments, where on-premises, public cloud, and private cloud coexist, are no longer an optional choice for enterprises but a practical standard. The challenge lies in how to establish consistent security policies in this complex environment and allow administrators to reliably control all access activities.
This document explains the fundamental principles of security architecture required in hybrid environments and provides concrete design approaches for implementation. It is written to convey not just individual functionalities but also how the security system operates in terms of flow and context.
In South Korea, approximately 700 deployment cases have been applied across public and private cloud environments, including the financial sector. These figures demonstrate that hybrid environment security architecture is already a practically verified framework. The structure described in this document is based on real implementations using DBSAFER.
Security Challenges in Hybrid Environments
Dissolution of Boundaries
Traditional security relied on network boundary models, such as firewalls and network segmentation. However, with cloud adoption, data and resources no longer reside within limited network boundaries. External SaaS, public cloud RDS, and container orchestration all undermine conventional boundary-based security models.
Difficulty in Applying Consistent Policies
Applying the same security policies across different resource types—on-premises assets, public cloud VMs, managed databases, and Kubernetes pods—is challenging. Account structures vary, and access paths are diverse.
Operational Complexity and Lack of Visibility
Security teams need a unified monitoring system to observe all access attempts in real-time and respond quickly. Hybrid environments require handling multiple administrative tools and control points simultaneously, which greatly increases operational complexity.
Security Architecture Design Principles
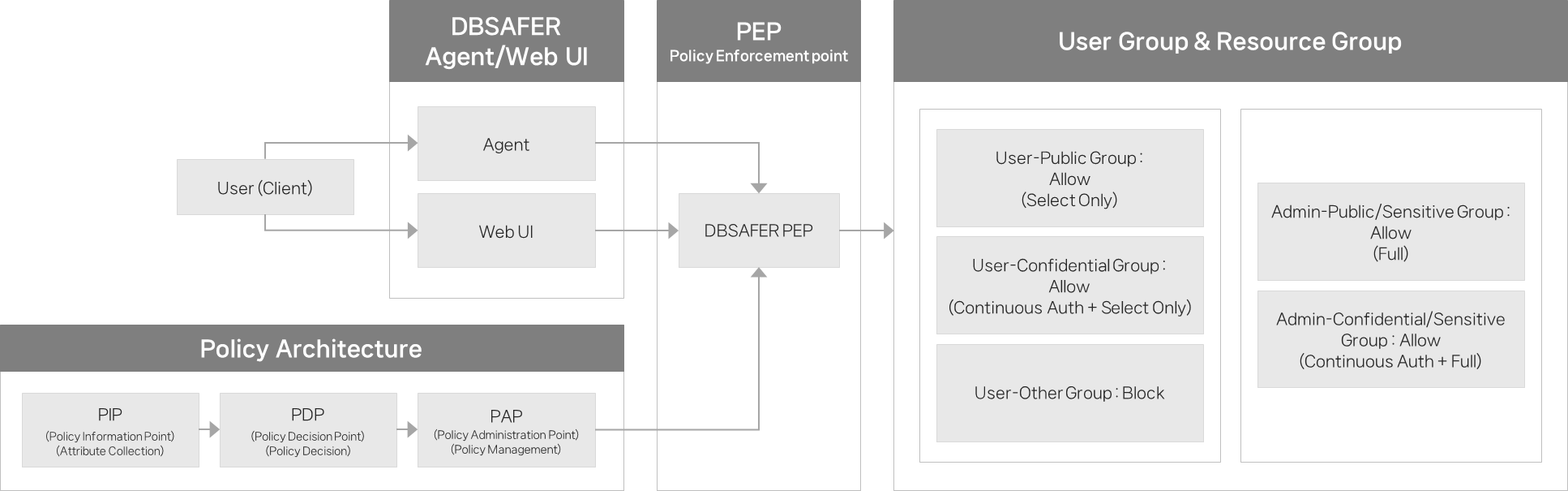
Single Control Point (PEP)
All access must pass through a Policy Enforcement Point (PEP). This ensures consistent enforcement of access controls regardless of resource type or physical location.
Attribute-Based Access Control (ABAC)
Attributes of users, resources, and environments are collected and evaluated (PIP, PDP, PAP) to dynamically control access. Policies change in real-time based on current risk levels and group attribute changes, moving beyond simple role-based authorization.
Automation and Provisioning
Resources are automatically registered or deregistered with the security system as they are created or deleted. Administrators do not need to add or remove them manually; security follows the resource lifecycle through APIs and scripts.
High Availability and Scalability
Security gateways must avoid single points of failure. Multi-AZ redundancy, load balancer integration, and dynamic port-based scalability ensure both reliability and performance.
Implementation Architecture
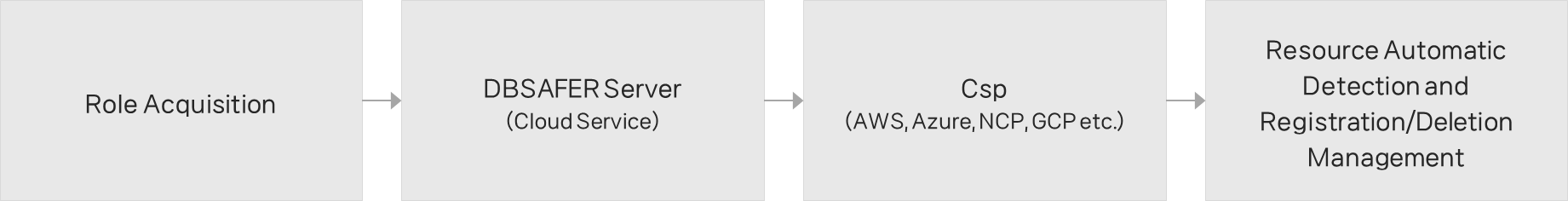
Resource Auto-Discovery (Public Cloud)
In public cloud environments, modules acquire role information and automatically detect resources accessible to the account, such as RDS and EC2 instances. Detected resources are automatically registered or deregistered as security objects. Administrators benefit from dynamic management without manual intervention.
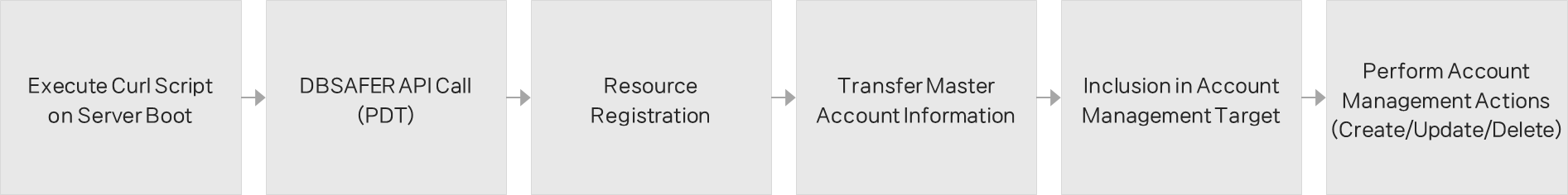
Resource Registration (Private Cloud)
In private cloud environments, a curl script runs during server boot to request registration with the security gateway’s RESTful API. Master account information is also provided. Resources are immediately incorporated into the account management system, allowing instant creation, modification, and deletion of accounts.
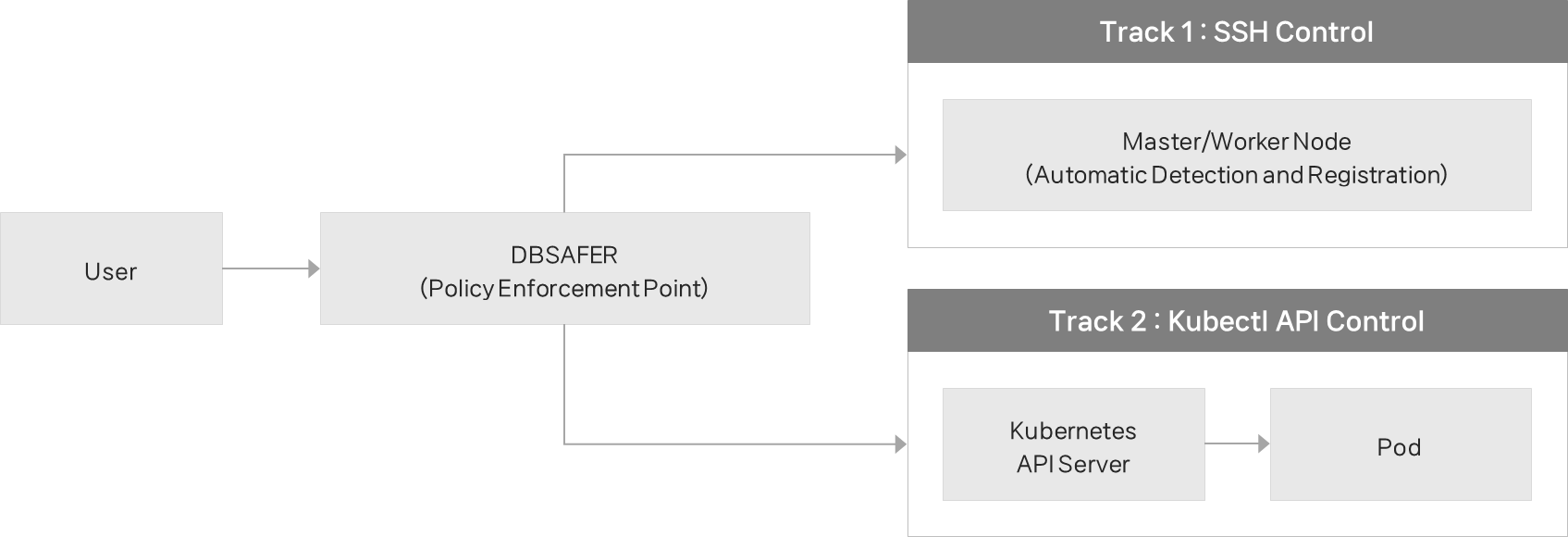
Kubernetes Security
Kubernetes environments enforce access control using two tracks:
Node/SSH
Master and worker nodes are automatically discovered and registered, and SSH access is controlled.
kubectl/API
Operator-executed kubectl commands translate into Kubernetes API calls that pass through the PEP for monitoring, control, and logging. This enables audit and enforcement down to individual command execution.
Group-Based Policies and ABAC
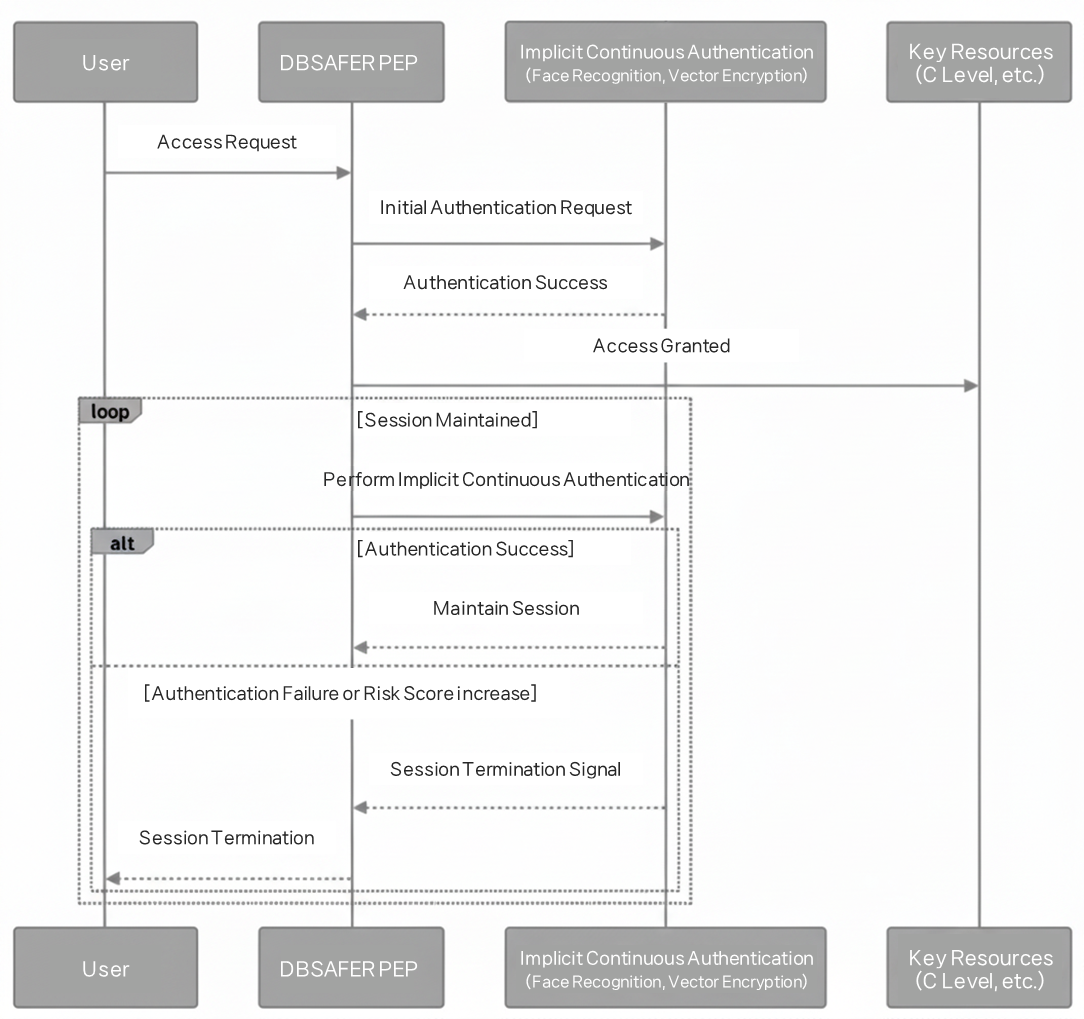
Users and resources are mapped in groups, and policies change according to group attributes and risk status. For example, access to confidential groups requires continuous authentication, and all sessions are terminated immediately if the risk score increases.
Implicit Continuous Authentication (ICA)
For critical resource access, users undergo face-recognition-based implicit continuous authentication. The data is encrypted in vector form, making it resilient against hacking. Authentication is periodically verified during sessions, and failed attempts result in immediate session termination.
High Availability and Operational Convenience
Security gateways operate reliably through Multi-AZ redundancy and integration with NLB/ALB. Dynamic port-based listener and target group management ensures scalability. Administrators can use both Web Manager and C/S Manager. Security events and approval procedures integrate seamlessly with messaging platforms like Slack via APIs.
Expected Benefits
Consistent Security Control
All resources across on-premises, public cloud, private cloud, and container environments are managed under a single control system. Administrators only need to focus on “which resource,” not “which environment,” eliminating policy gaps and blind spots.
Operational Efficiency
Automated discovery, registration, and API-based provisioning minimize repetitive administrative tasks. Policies are automatically reflected even in environments with frequent resource creation and deletion, reducing operational fatigue.
Regulatory Compliance and Audit Readiness
All access passes through the PEP for record-keeping and audit. Implicit ontinuous authentication and group-based policies enhance the protection of sensitive assets. Logs are centralized and standardized, meeting regulatory requirements in financial and public sectors, and real-time policy enforcement strengthens internal control compliance.
High Availability and Reliability
Multi-AZ redundancy and load balancer-based scaling eliminate single points of failure and ensure service continuity.
Enhanced User Experience
Implicit continuous authentication allows users to maintain sessions without repeated authentication, balancing strong security with convenience.
Practical Verification and Trustworthiness
Approximately 700 deployment cases, including in the Korean financial sector, have verified the architecture’s stability and scalability.
Conclusion
Security in hybrid environments is not a set of individual functions but the result of consistent architecture design. All access passes through the PEP, policies are dynamically determined based on attributes, and resources are automatically discovered, registered, and managed. Implicit continuous authentication and ABAC achieve both operational convenience and security strength. DBSAFER exemplifies a platform implementing these principles.
This document helps readers understand the framework for hybrid environment security approaches.
