Strengthening Zero Trust Security through Implicit Continuous Authentication (ICA)
PNPSECURE’s ICA (Implicit Continuous Authentication) leverages Vision AI to verify users in real time, closing MFA security gaps and enabling continuous Zero Trust authentication.
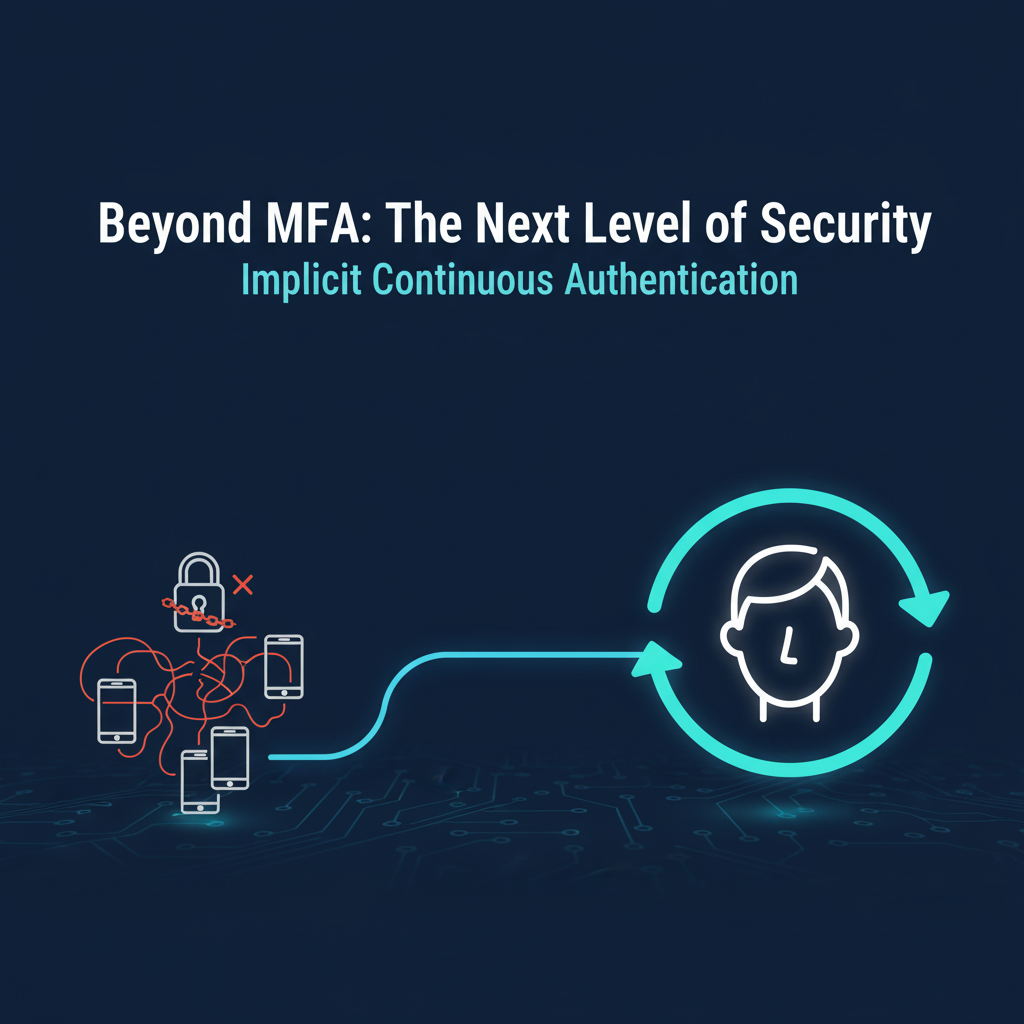
PNPSECURE’s ICA (Implicit Continuous Authentication) is an AI-based authentication technology that fundamentally overcomes the limitations of traditional MFA.
Unlike MFA, which performs static verification only at login, ICA provides a dynamic, session-wide trust validation mechanism that continuously authenticates users throughout their entire session.
In other words, ICA has evolved from “authentication at login” to “authentication across the session.”
This enables real-time detection and prevention of account takeovers and insider misuse — even after initial authentication — without interrupting user workflows.
Limitations of Traditional MFA
Traditional MFA focuses solely on initial login. Once a session is established, there are no additional checks to validate identity.
This structural limitation allows attackers to exploit long-lived sessions or shared accounts without triggering reauthentication.
Moreover, frequent user prompts disrupt productivity. Simply put, “one-time authentication” is no longer secure.
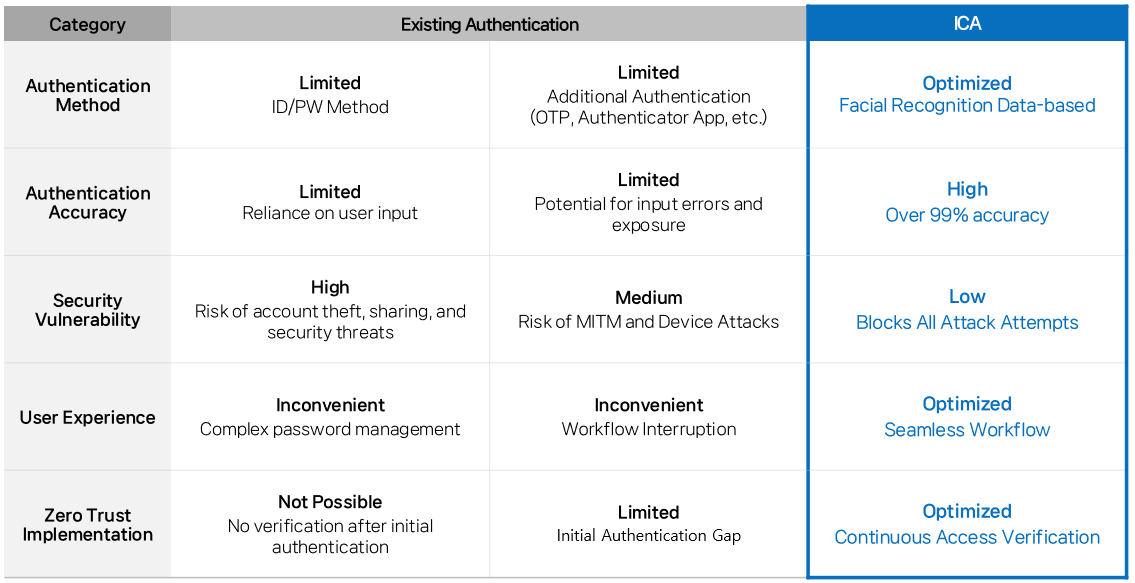
A New Paradigm: ICA’s Continuous Authentication
ICA eliminates these authentication gaps by enabling continuous, automated verification throughout every session.
The process operates seamlessly in the background, requiring no user input while enhancing accuracy through AI-driven analysis.
By continuously validating user identity even after login, ICA blocks unauthorized commands and abnormal actions in real time — achieving both security continuity and user convenience.
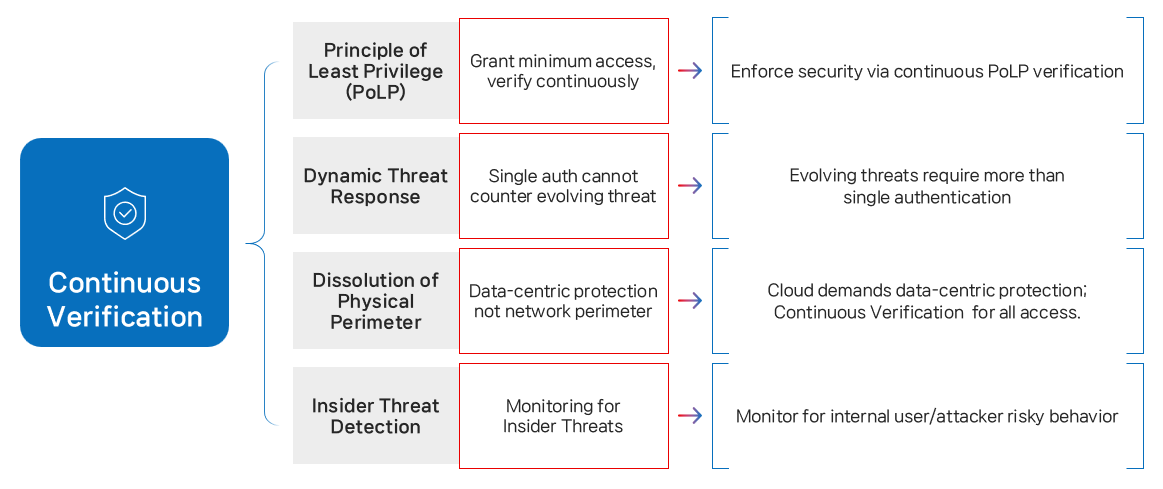
The Need for Continuous Verification
In 2023, the Korean government’s “Zero Trust Guideline 2.0” identified Continuous Verification as an essential Zero Trust principle.
To achieve this, identity must be validated without user involvement and without authentication gaps throughout a session.
Here, the concept of “Implicit” becomes critical.
The system must automatically confirm user identity through AI, without requiring any explicit action from the user.
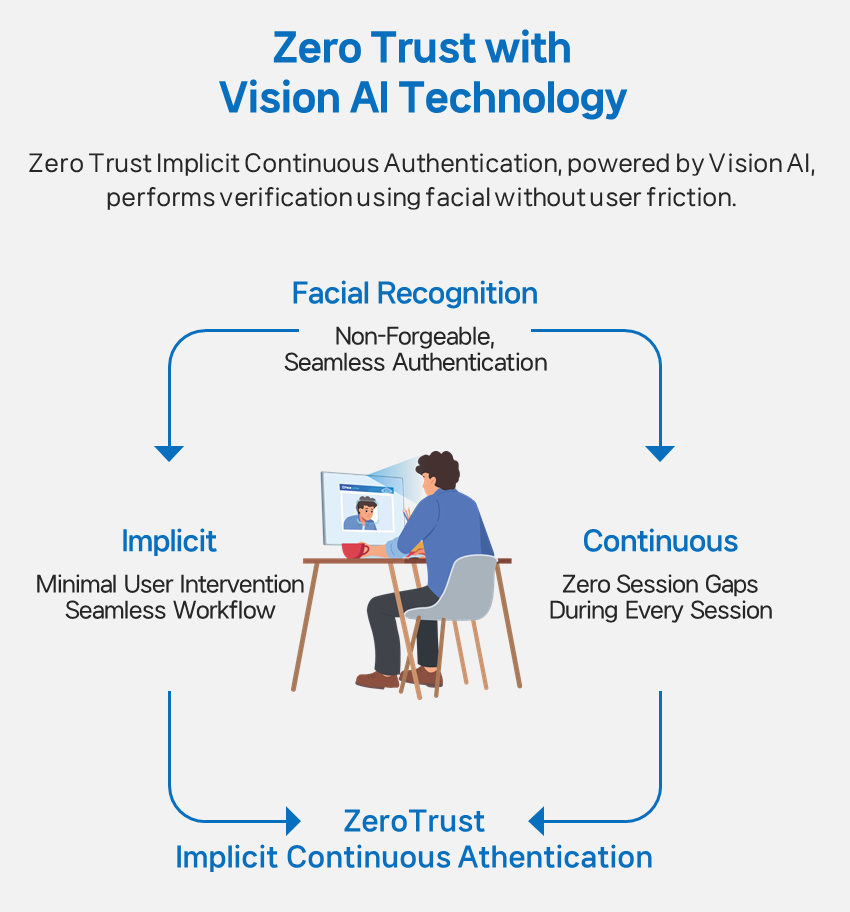
What Is ICA (Implicit Continuous Authentication)?
ICA is an AI-based authentication technology independently developed by PNP Secure using Vision AI.
It verifies user identity in real time simply by analyzing facial vectors as the user looks at the screen.
While MFA verifies only at login, ICA continuously validates identity throughout the entire session.
- Implicit: No user intervention is needed.
- Continuous: Eliminates authentication blind spots.
- AI-driven: Detects anomalies automatically.
By integrating these three principles, ICA overcomes the inherent limitations of MFA—such as workflow disruption—and brings the Zero Trust model into practice.
The technology is applied to PNP Secure’s DBSAFER DB (database access control) and DBSAFER AM (system access control) solutions, ensuring uninterrupted identity validation throughout the entire session.
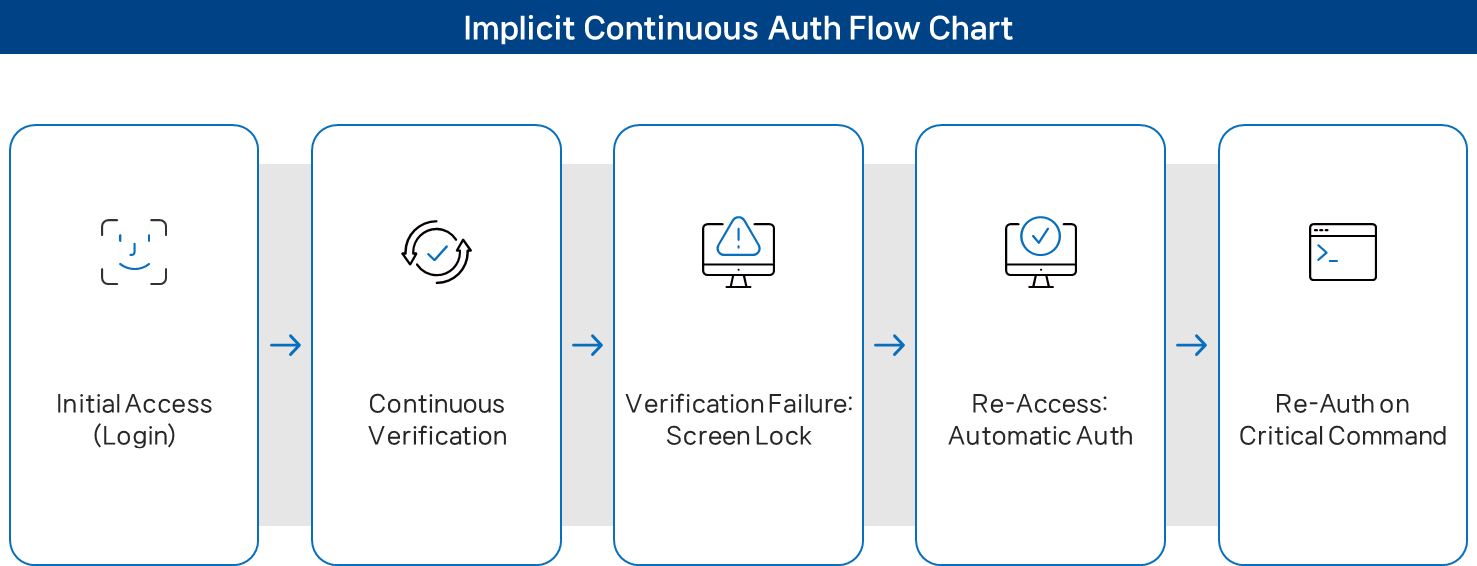
How ICA Works
- Initial Authentication: User logs in via standard credentials or MFA.
- Continuous Verification: ICA analyzes facial vector data throughout the session, confirming authorization at command-level granularity.
- Anomaly Detection & Response: When behavior deviates from the user’s normal pattern, ICA automatically locks the session or requests reauthentication.
Vision AI Architecture of ICA
The core of ICA is Vision AI—intelligent video-based recognition.
- Face Detection: Captures the user’s face via webcam.
- Vectorization: Converts facial features into a vector and compares them to stored identity data.
- Response: If the user leaves or an unauthorized person appears, the system instantly locks or blocks access.
Unlike simple facial login, ICA involves AI across the entire cycle of perception → behavior analysis → prevention.
It prevents unauthorized recording, screen sharing, and account hijacking in real time.
Defense Against Hacking and Insider Threats
Lateral Movement attacks, where intruders expand privileges inside the network, pose major security risks.
ICA prevents such attacks by validating each command within the session.
Even if an attacker hijacks an active session, they fail the continuous authorization checks and are immediately blocked.
Additionally, when a legitimate user leaves their seat, the system detects absence and automatically locks access, stopping insider misuse.

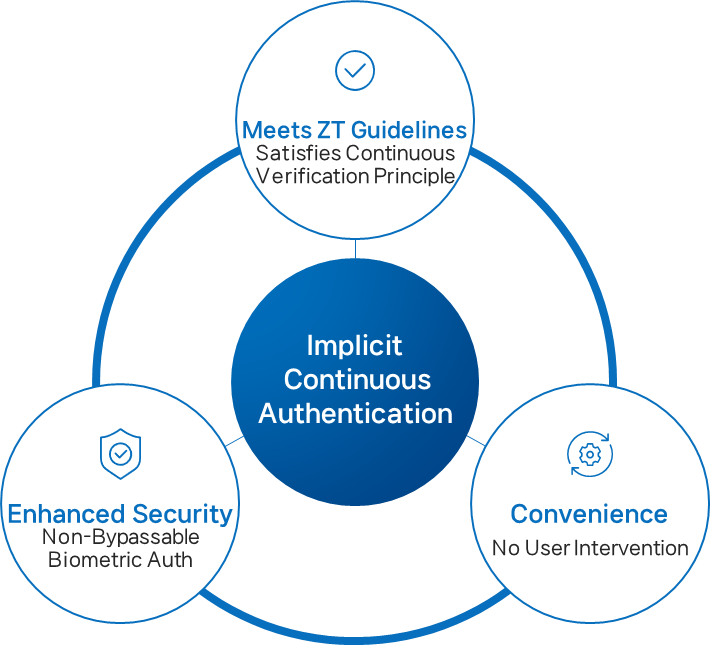
Proven Security and Efficiency Gains
ICA is more than an authentication feature—it’s a core framework for implementing Zero Trust through continuous verification.
Key Outcomes:
- Enhanced Security: Eliminates authentication gaps with real-time verification.
- Seamless Usability: Maintains workflow through non-intrusive, implicit validation.
- True Zero Trust Implementation: Ensures ongoing trust across users, devices, and sessions.
Proven in Enterprise Environments
ICA has already been successfully deployed in large enterprise environments, including finance and public sectors, where it demonstrated reliability and accuracy.
Organizations recognize ICA as a critical enabler of Zero Trust by closing the authentication gap and strengthening internal security.
Future Roadmap
ICA is already proving to be a practical Zero Trust enabler, combining implicit authentication and continuous verification.
Moving forward, PNP Secure aims to expand ICA into a context-aware intelligent authentication model, integrating behavioral, environmental, and access context data for holistic verification.
This evolution will transform ICA from a “login validation” mechanism into a real-time behavioral security platform.
Additionally, by diversifying Vision AI training datasets and ensuring interoperability with international standards, ICA seeks to establish itself as a global benchmark for sustainable identity security ecosystems.
