Cloud Lateral Movement Control Strategies in Cloud Environments
Explore cloud lateral movement threats and learn how DBSAFER’s multi-layered defense strategy secures workloads, prevents lateral attacks, and ensures safe multi-cloud operations.

Cloud Expansion and Emerging Security Challenges
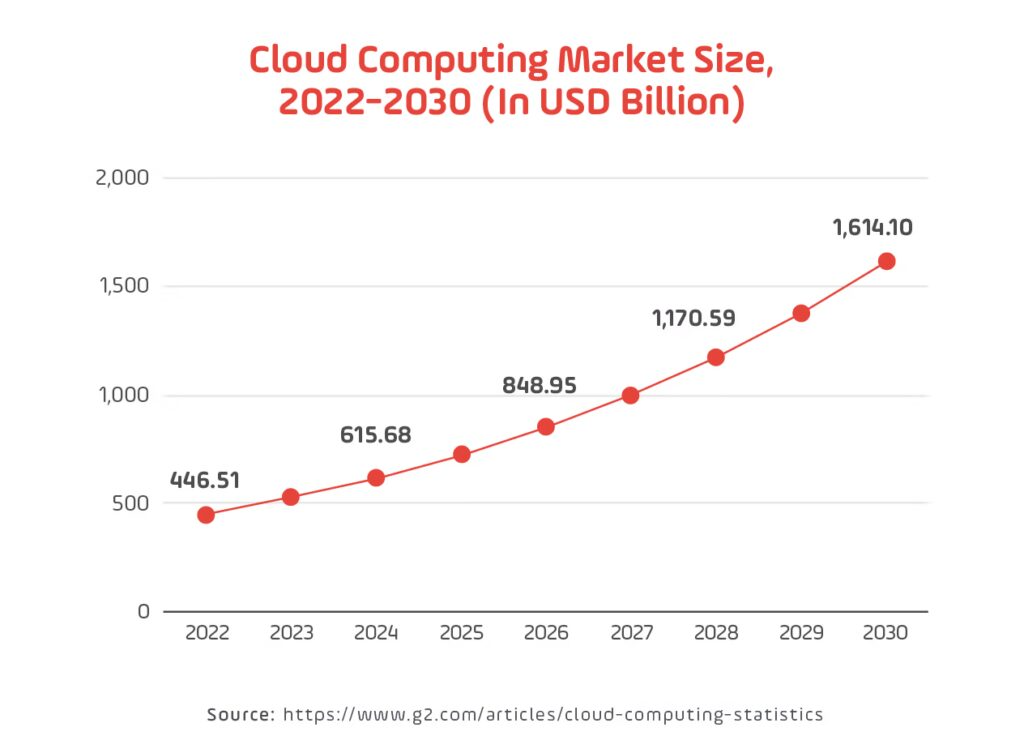
In today’s business environment, cloud computing has become an essential component. Companies are rapidly adopting cloud solutions to enhance business agility, increase operational efficiency, and accelerate innovation. According to Gartner, global public cloud end-user spending is projected to reach USD 723.4 billion by 2025. Additionally, a survey by Edge Delta indicates that 94% of companies worldwide have adopted cloud computing.
However, this cloud expansion brings new security challenges. Advanced Persistent Threat (APT) attacks are becoming more sophisticated and covert. After initial infiltration, attackers move laterally within the internal network (lateral movement) to attempt access to critical assets.
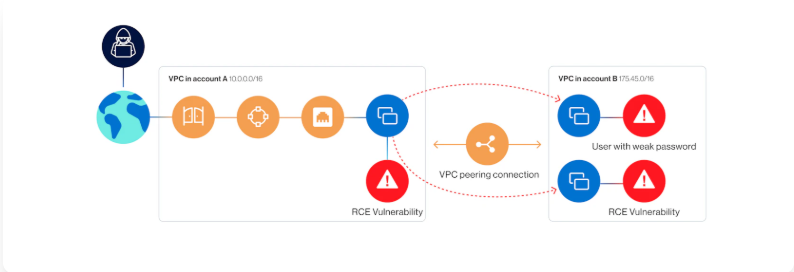
Cloud environments’ dynamic and distributed architecture, API-based resource management, and virtualized network characteristics make detecting and blocking lateral movement difficult. More than 90% of large enterprises operate multi-cloud environments, exponentially increasing security management complexity.
Real-World Threats of Lateral Movement in Cloud Environments
Movement from Compromised VMs/Containers
Attacks often start through vulnerabilities in a single virtual machine (VM) or container. Once attackers gain control of one workload, they begin internal reconnaissance. According to Wiz, attackers use built-in commands such as whoami, ifconfig, and net view to check current privileges and network configuration. Based on this information, they attempt to access other VMs or containers within the same network, gradually moving toward servers containing critical data.
Account Compromise and Privilege Escalation
Accounts represent one of the most potent attack vectors in cloud environments. Attackers steal cloud account credentials of developers or system administrators via phishing or exploiting vulnerabilities. If these accounts have excessive privileges, attackers can create new VMs, replicate other users’ disk snapshots, and access sensitive information, performing lateral movement in ways indistinguishable from legitimate administrative activity.
Advanced Backdoor Cases: BPFDoor
Sophisticated backdoors like BPFDoor pose severe threats to cloud security. BPFDoor exploits the Linux kernel’s Berkeley Packet Filter (BPF) to monitor network traffic at the kernel level. When receiving a specific signal called a "magic packet," the backdoor activates, granting remote access to attackers. BPFDoor bypasses application-level security solutions, making detection, tracking, and blocking extremely difficult. Once installed, it can remain dormant, providing attackers with a covert channel for future infiltration and internal data theft.
Stealth Data Exfiltration and Session Hijacking
The ultimate goal of lateral movement is often data exfiltration. Attackers move freely within the network, accessing core assets such as database and file servers to steal confidential information. They may also hijack active user sessions (Session Hijacking) to execute malicious commands without additional authentication. These activities occur within normal traffic patterns, making detection with conventional network security tools nearly impossible.
Security Complexity in Multi-Cloud Environments
Inconsistent CSP Policies and Management Complexity
Organizations increasingly adopt multi-cloud strategies to avoid dependency on a single cloud provider (CSP) and leverage the best services from multiple CSPs. However, multi-cloud environments complicate security management and present attackers with more opportunities. AWS, Azure, and Google Cloud each employ unique security models, tools, and terminology, making it challenging for security teams to establish consistent policies. IBM reports that 40% of data breaches involve data spread across multiple environments, highlighting the vulnerability of distributed security management.
Challenges in IAM and Access Control
Identity and Access Management (IAM) is particularly challenging in multi-cloud environments. Manually managing IAM policies across different clouds often leads to over-privileged users or services. SentinelOne statistics indicate that more than half of organizations lack sufficient access restrictions, creating a high-speed lane for attackers to extend lateral movement once an account is compromised.
Absence of Network Segmentation
While physical network segmentation enhances security on-premises, cloud environments require logical micro-segmentation to control lateral movement. Without proper network segmentation, attackers gaining control of a single workload can move freely across systems, rendering lateral movement virtually undetectable.
DBSAFER Perspective: Unified Security Gateway for Consistent Control
To address the complexity of multi-cloud environments, DBSAFER provides a CSP-independent approach. Acting as a protocol-aware security gateway, DBSAFER centrally controls all server access traffic, enforcing consistent security policies and enhancing visibility and control across heterogeneous cloud environments.
Control Strategies: Necessity of Multi-Layer Defense
Lateral movement in cloud environments requires an integrated, multi-layer defense strategy rather than reliance on a single security solution. DBSAFER implements key elements of this approach:

Micro-Segmentation: Minimizing Lateral Paths
Micro-segmentation divides networks into smaller units to minimize inter-workload communication. DBSAFER manages workloads across multi-cloud networks, reducing potential lateral movement paths and enforcing least privilege within security boundaries.
Zero Trust Architecture: Continuous Verification
Zero Trust principles dictate "never trust, always verify." DBSAFER provides continuous authentication, validating user sessions even after initial login, requiring additional verification for sensitive actions, thereby minimizing potential damage from compromised credentials.
Strong IAM: Enforcing Least Privilege
DBSAFER logs all user activities to verify adherence to least privilege principles. Administrators can track who accessed which systems, executed commands, and identify abnormal behaviors, providing critical evidence for tracing lateral movement paths.
Cloud Security Response Strategies Using DBSAFER
Centralized Security Management
- Unified Dashboard: Real-time monitoring of all servers across AWS, Azure, and on-premises from a single dashboard.
- Consistent Policy Enforcement: Standardized security policies across diverse CSP environments.
- Detailed Log Analysis and Behavior-Based Detection: Captures all user access, command executions, and system responses to identify lateral movement.
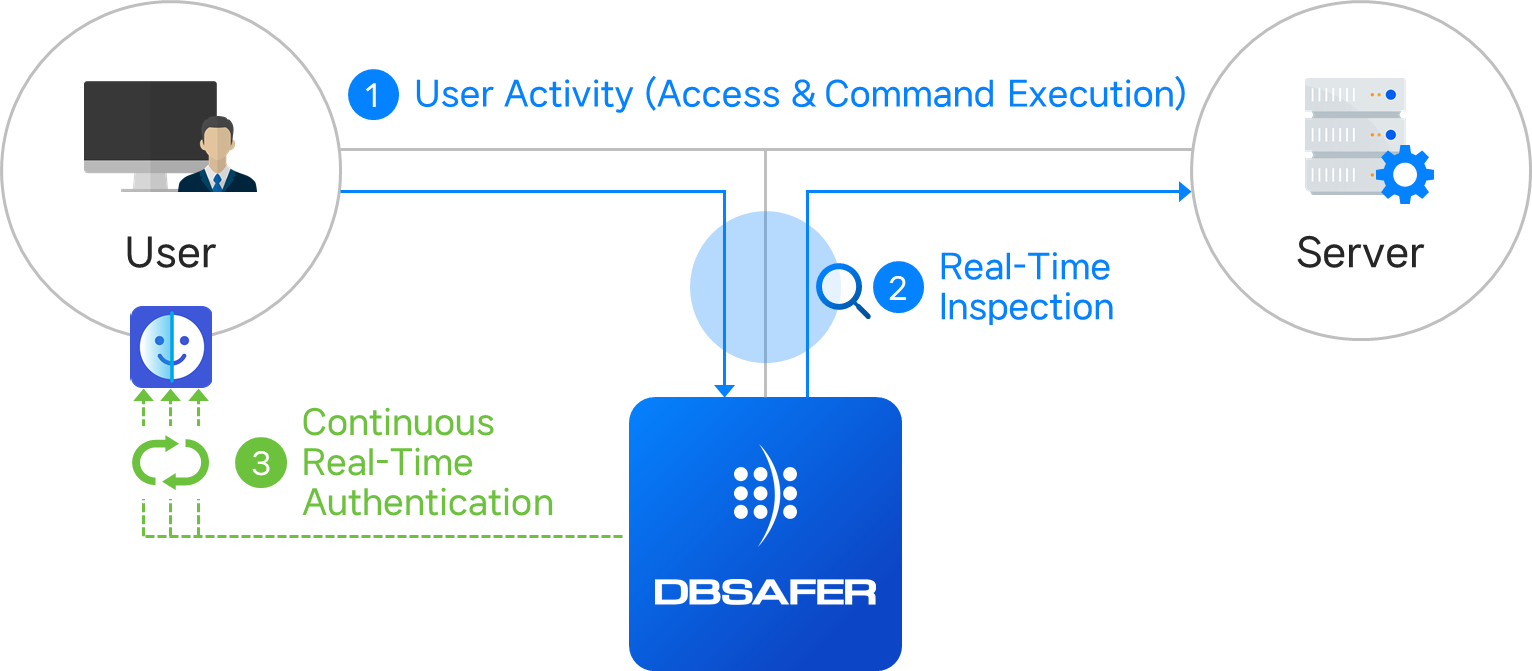
User Session Management and Behavior-Based Authentication
DBSAFER proxies user sessions to servers, continuously monitoring activities and enforcing stepwise authentication for sensitive operations, maintaining robust security.
Automation and Orchestration for Proactive Response
- Real-Time Asset Identification: Detects new cloud assets and applies security policies automatically.
- Automated Server Checks: Periodically scans configurations, processes, and files to detect threats like BPFDoor.
- Real-Time Alerts and Response: Notifies administrators immediately upon detecting anomalies.
Blocking Backdoor Spread
- Hidden Traffic Blocking: Detects abnormal protocol signals and blocks them at the gateway.
- Session Hijack Defense: Continuous authentication prevents attackers from exploiting hijacked sessions.
Conclusion: DBSAFER, Optimal Solution for Cloud Lateral Movement
As cloud environments grow complex, attackers find more hiding places, and defenders face increased challenges. Lateral movement exploits this complexity. DBSAFER combines centralized control, detailed log analysis, and automated proactive measures to effectively manage the entire lateral movement process. By blocking high-level backdoors like BPFDoor, DBSAFER delivers the most efficient and robust security strategy for multi-cloud environments. With DBSAFER, companies can enjoy cloud agility while protecting critical assets.
References
- 2024 Cloud Threat Landscape Report: How does cloud security fail? – IBM
- Gartner Forecasts Worldwide Public Cloud End-User Spending – 2024
- Preventing Lateral Movement Techniques – Google Cloud
- Rise of Multi-Cloud Strategies – Growin, 2025
- Understanding Lateral Movement – Wiz
- Cloud Security Statistics 2025 – SentinelOne
- Cloud Computing Adoption 2024 – Edge Delta
